Overview of database security assessment
Database security assessment involves assessing the security of your database systems to identify and mitigate vulnerabilities. This process ensures that sensitive data stored in databases is protected from unauthorized access, breaches, and other security threats. It includes analyzing database configurations, user permissions, and data encryption practices.

Importance of proactive security measures
Proactive security measures are necessary for safeguarding databases against cyber threats. Regular security assessments help identify potential vulnerabilities before they can be exploited by attackers. Implementing proactive measures reduces the risk of data breaches, financial losses, and reputational damage, ensuring the integrity and confidentiality of sensitive information.
Key objectives and benefits
The main objectives of database security assessment are to identify security weaknesses, ensure compliance with industry regulations, and protect sensitive data. Benefits include improved database security, reduced risk of data breaches, and enhanced compliance with standards such as GDPR and HIPAA. Regular assessments help maintain a robust security posture.
Identification of typical database vulnerabilities
Typical database vulnerabilities include SQL injection, misconfigurations, excessive user privileges, and unpatched software. These weaknesses can be exploited by attackers to gain unauthorized access, manipulate data, or disrupt database operations. Identifying these vulnerabilities is critical for implementing effective security measures.
Examples:
Examples of database vulnerabilities include SQL injection, where attackers inject malicious SQL code to manipulate the database, and misconfigurations, such as default settings that expose sensitive data. Excessive user privileges can also lead to unauthorized data access, while unpatched software leaves databases exposed to known exploits.
Real-world consequences of data breaches
Data breaches can have severe real-world consequences, including financial losses, legal penalties, and damage to an organization’s reputation. For instance, a healthcare database breach could expose patient records, leading to privacy violations and regulatory fines. Ensuring strong database security prevents such incidents and protects sensitive information.
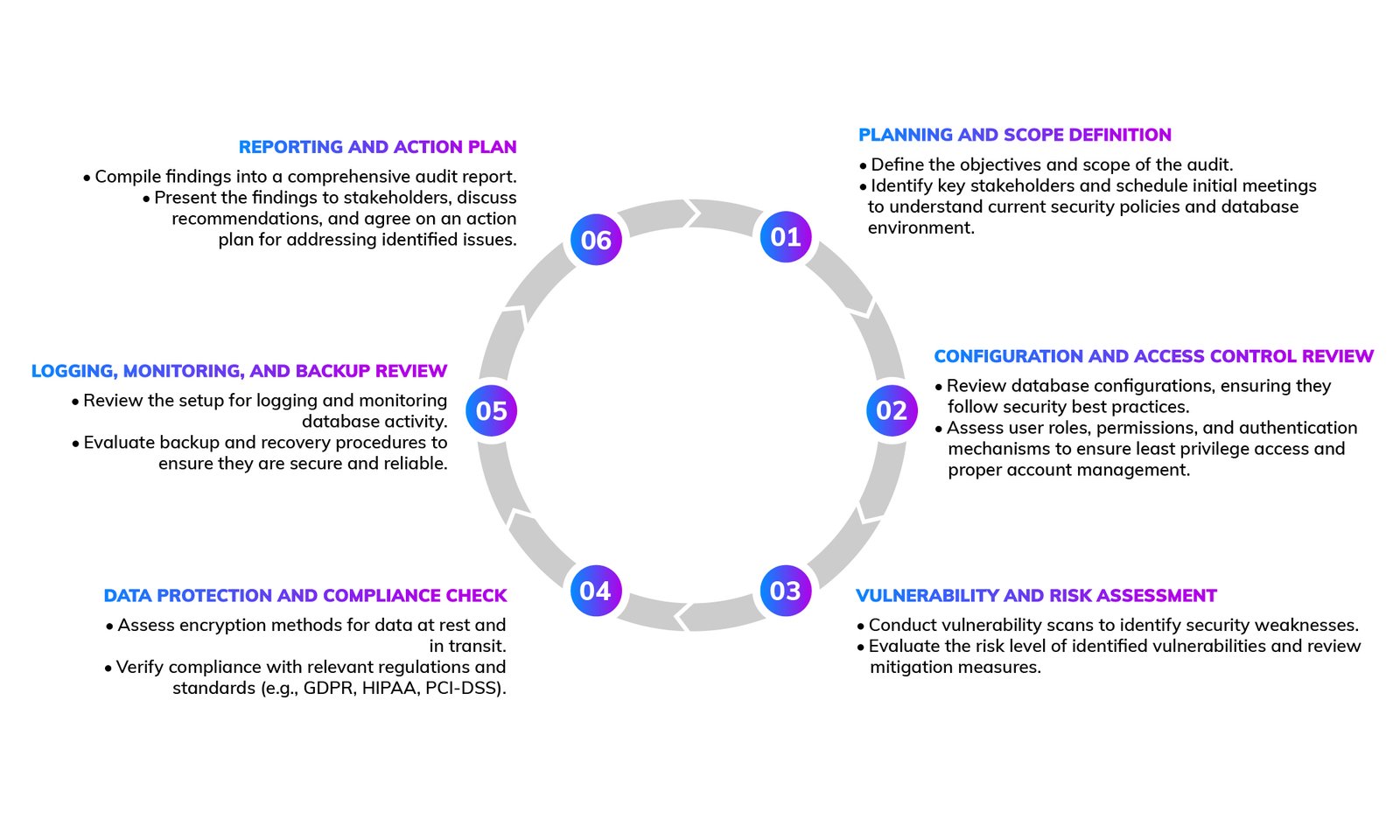
The Database Security Assessment Process
Don't Be the Next Victim
Secure your most valuable data and assets with Lumiverse Solutions!
Tools and Techniques for Database Security
Overview of industry-leading security tools
Industry-leading tools for database security assessment include Nessus, SQLMap, and DBShield. Nessus scans for vulnerabilities and compliance issues, SQLMap automates the detection and exploitation of SQL injection flaws, and DBShield provides real-time database activity monitoring and anomaly detection. These tools help identify and mitigate security risks.
Techniques for assessing database security posture
Techniques for assessing database security posture include vulnerability scanning, penetration testing, and configuration reviews. Vulnerability scanning identifies potential security weaknesses, while penetration testing simulates real-world attacks to evaluate the database's defenses. Configuration reviews ensure that database settings follow security best practices.
Considerations for in-house vs. outsourced assessments
Choosing between in-house and outsourced assessments depends on available resources, expertise, and budget. In-house assessments offer greater control and familiarity with the database environment, while outsourced assessments provide access to specialized expertise and advanced tools. Combining both approaches can enhance security
Why Choose Professional Security Services
Compliance with industry regulations
Professional penetration testing services ensure that your mobile application complies with industry standards, such as the OWASP Mobile Top 10. Adhering to these standards helps protect user data and reduces the risk of security breaches. Compliance demonstrates your commitment to security and builds user trust.
Comprehensive reporting and actionable insights for developers
Client Experiences That Shine!
Genuinely robust solutions, effectively detected and neutralized potential threats, providing a sense of confidence in the ever-evolving landscape of cybersecurity. The responsive customer support and commitment to staying ahead of emerging risks make them a reliable choice for businesses seeking top-notch protection.