- Home
- About
- Services
Expert Cybersecurity Services You Can Rely On
Guardians of the Digital Realm, Keeping Threats at Bay.
Empower Your Security Strategy: Introducing the Pioneers in
Assessment Services!Battle-Tested Cyber Guardians: Unveiling the Elite in Incident
Response!Expert Guidance for Cyber Security Compliance: Introducing Our Consulting Services
Security
OperationsUnderstanding Security Operations: Navigating the Cybersecurity Landscape
Getting Started with Specialized Cybersecurity Services: An Introductory Framework

Expert Cybersecurity Services You Can Rely On
Guardians of the Digital Realm, Keeping Threats at Bay.
Empower Your Security Strategy: Pioneers in Assessment Services!
Battle-Tested Cyber Guardians: Unveiling the Incident Response!
Expert Guidance for Cyber Security Compliance: Our Consulting Services
Security
Operations >>Security Operations: Navigating the Cybersecurity Landscape
Specialized Cybersecurity Services: An Introductory Framework
- Industry
Empowering Industry, Securing Tomorrow
Unveiling the Industry Menu: Your Gateway to Cyber Security Solutions!

Empowering Industry, Securing Tomorrow
Unveiling the Industry Menu: Your Gateway to Cyber Security Solutions!
- Contact
Fortify Your Network - Uncover Vulnerabilities Before Attackers Do!
Your network is the backbone of your organization. Ensure it’s impenetrable with our comprehensive Network Penetration Testing services. Detect weak points, safeguard your data, and stay one step ahead of cyber threats.
Understanding Network Penetration Testing
Network Penetration Testing, also known as pen testing or ethical hacking, is a visionary security measure where simulated cyberattacks are conducted to identify and handle vulnerabilities in a network.
This process helps organizations find weaknesses in their network security and provides actionable insights to strengthen defenses. Using penetration testing services, businesses can actively address security gaps before hackers manipulate them.

Importance of Regular Security Assessments:
Regular security assessments are essential for maintaining a strong security posture. As cyber threats evolve, so do the tactics and techniques used by attackers. Conducting frequent network security assessments helps organizations stay ahead of potential threats, ensuring that security measures are up-to-date and effective. This ongoing evaluation is essential for protecting sensitive data, maintaining compliance, and securing the stability of the network. Network Penetration Testing.
Key Objectives and Benefits:
The key objectives of network penetration testing are to identify vulnerabilities, consider their potential impact, and provide recommendations for mitigation. Providing benefits like enhanced security, improved risk management, and compliance with industry standards.
By understanding and addressing vulnerabilities, organizations can reduce the risk of data breaches, minimize operational disruptions, and protect their reputation. Ethical hacking for networks provides a visionary approach to cybersecurity and protects the business’s critical assets. Network Penetration Testing.
Common Network Vulnerabilities
Network vulnerabilities can occur from various sources, including misconfigurations, weak passwords, outdated software, and unpatched systems. Attackers can exploit these vulnerabilities to gain unauthorized access, disrupt services, or steal sensitive data. Regular network vulnerability assessments help identify and address these weaknesses, providing a secure network environment.
Examples:
Misconfigurations, such as improper firewall settings or insecure default configurations, can expose networks to cyber threats. Weak passwords are another common vulnerability, making it easy for attackers to gain access through a systematic approach or password-guessing attacks.
Real-World Consequences of Exploitation
The exploitation of network vulnerabilities can lead to severe consequences, including data breaches, financial losses, and reputational damage. Cyber attackers can exploit misconfigurations to gain unauthorized access, disrupt services through denial-of-service attacks, or steal sensitive information.
These incidents can result in costly recovery efforts, legal penalties, and loss of customer trust. Regular network penetration testing helps prevent such incidents by identifying and addressing security weaknesses before they can be exploited.
Process of Network Penetration Testing
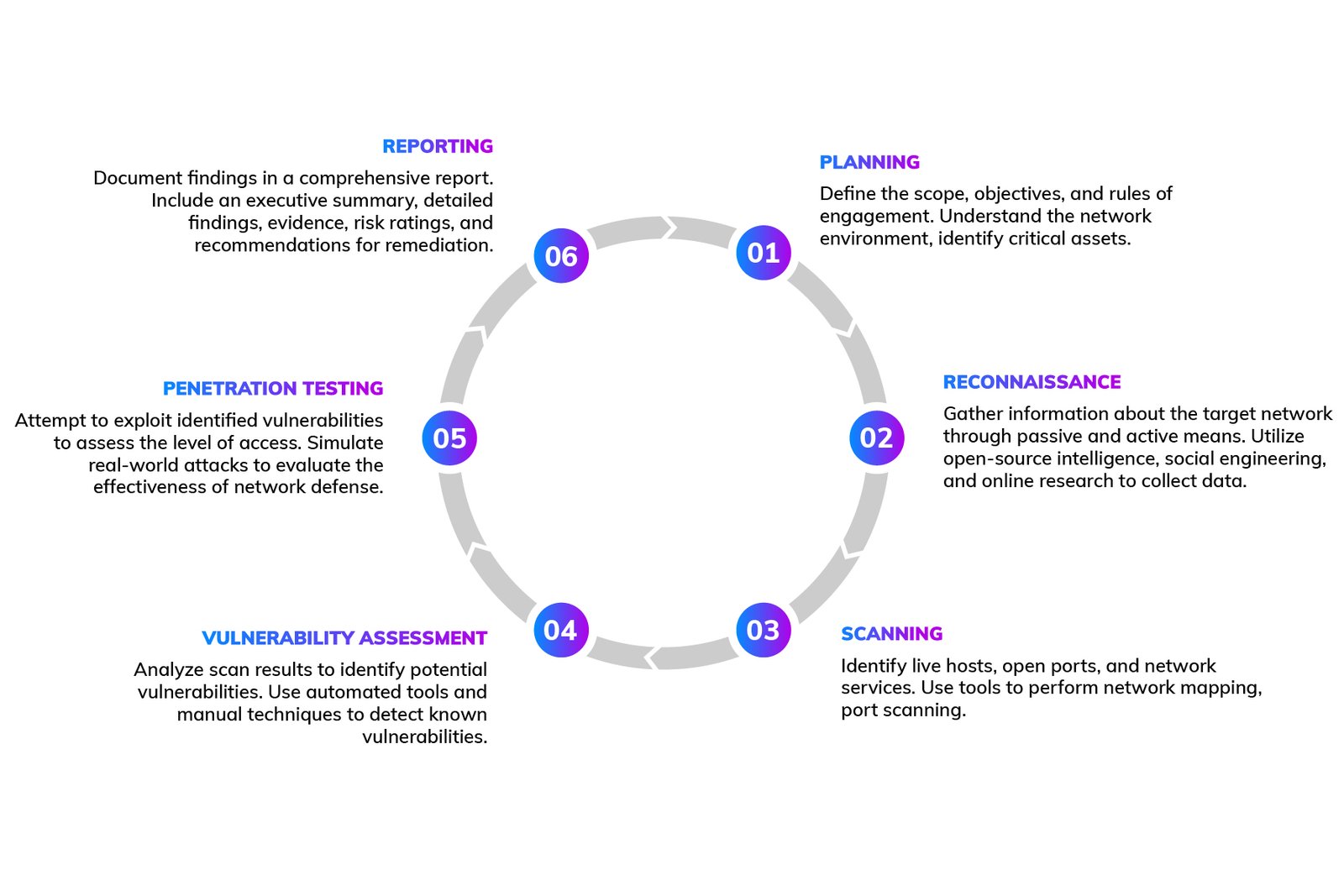
Ready to strengthen the security of your software?
Secure your most valuable data and assets with Lumiverse Solutions!
Choosing the Right Penetration Testing Tools
Overview of Popular Tools and Frameworks
Choosing the right tools and frameworks is necessary for effective network penetration testing. Popular tools include Nmap for network scanning, Nessus for vulnerability assessment, Metasploit for exploitation, and Wireshark for packet analysis. These tools provide comprehensive capabilities for identifying and exploiting network vulnerabilities. Understanding the strengths and limitations of each tool is required for conducting thorough and accurate assessments. Network Penetration Testing.
Criteria for Selecting the Appropriate Toolset
Selecting the appropriate toolset for penetration testing involves considering factors such as the scope of the assessment, the specific vulnerabilities to be targeted, and the expertise of the testing team. Criteria include the tool's ability to identify and exploit vulnerabilities, ease of use, integration with other security tools, and support for different operating systems and network environments. A well-chosen toolset provides a thorough and effective penetration testing process.
Considerations for In-House vs. Outsourced Testing
Deciding between in-house and outsourced penetration testing involves weighing the benefits and challenges of each approach. In-house testing provides greater control over the assessment process and can be cost-effective for organizations with skilled security teams. However, outsourced testing offers access to specialized expertise, advanced tools, and an external perspective on security. Both approaches have their merits, and the choice depends on the organization's specific needs and resources. Network Penetration Testing.
Why Partner with a Professional Security Firm
Compliance with Industry Standards
Professional security firms ensure compliance with industry standards, such as NIST, ISO, and other regulatory frameworks. They are well-versed in the requirements of these standards and provide assessments that align with best practices. Compliance with industry standards is required to maintain regulatory adherence, avoid legal penalties.