Understanding Web Application Penetration Testing What is it?
Web application penetration testing is a simulated cyberattack on your web applications designed to identify security weaknesses. This visionary approach helps find vulnerabilities that could allow attackers to steal data, disrupt operations, or compromise user privacy. It involves a thorough assessment of the application’s code, configuration, and functionalities to uncover potential security gaps before they are exploited by malicious actors.

Purpose and objectives of penetration testing
The primary objective of web application penetration testing is to enhance the security posture of web applications. It aims to identify and address vulnerabilities that could lead to data breaches, financial losses, and reputational damage. This testing provides compliance with industry regulations and data protection requirements. By simulating real-world attacks, organizations can understand the potential impact of security flaws and take corrective measures to prevent exploitation.
Types of vulnerabilities targeted
Web application penetration testing targets a wide range of vulnerabilities, including SQL injection, cross-site scripting (XSS), insecure authentication, and session management flaws. Other common vulnerabilities include security misconfigurations, sensitive data exposure, and insufficient logging and monitoring. By identifying these weaknesses, penetration testing helps organizations prioritize and remediate critical security issues, thereby reducing the risk of cyberattacks
Key Steps in Web Application Penetration Testing
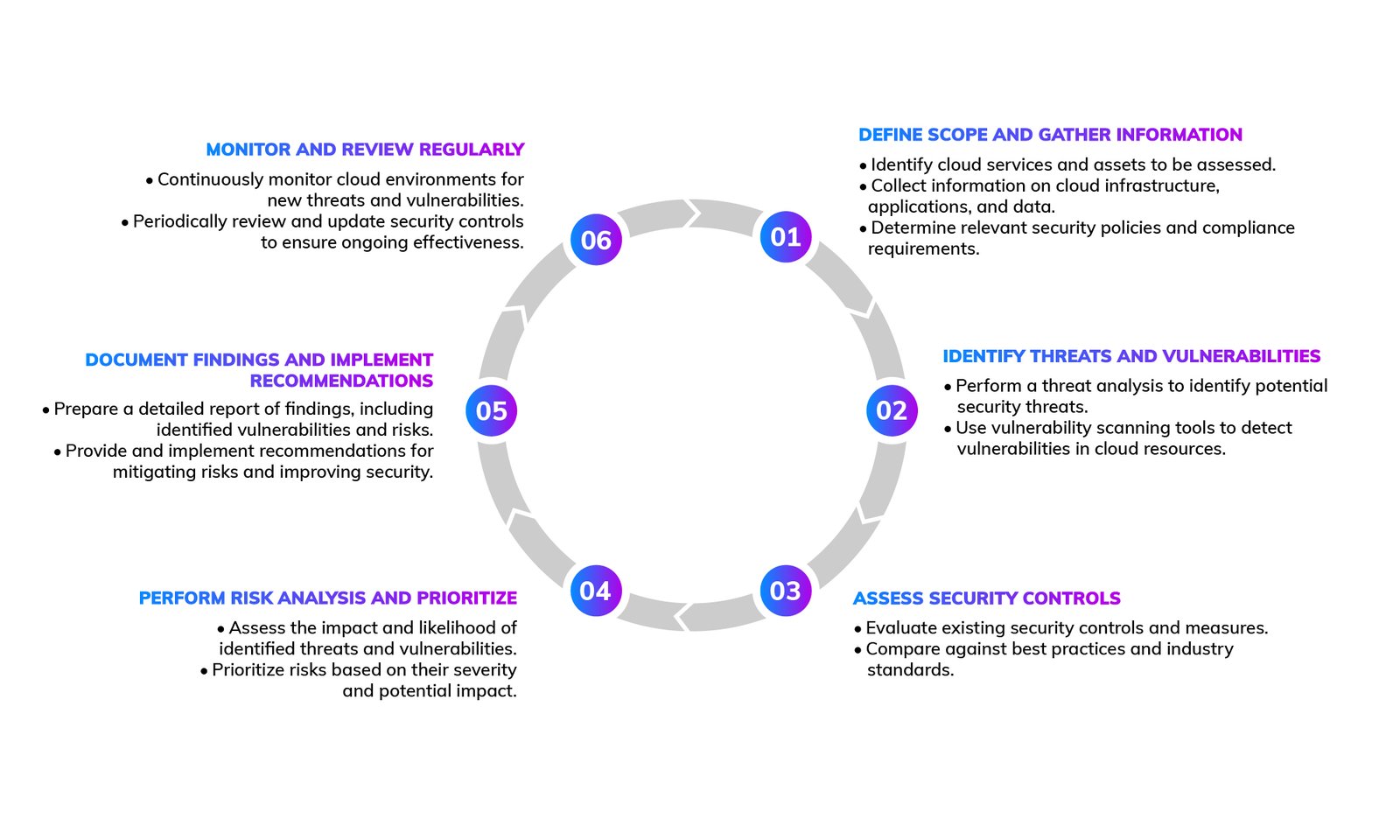
Planning and reconnaissance
The first step in web application penetration testing involves planning and reconnaissance. This phase includes gathering information about the target application, such as its architecture, technology stack, and potential entry points. Understanding the application’s functionality and identifying potential vulnerabilities is important for designing effective test cases and strategies.
Vulnerability scanning and analysis
In this phase, penetration testers use automated tools and manual techniques to scan the application for vulnerabilities. This includes identifying common issues like SQL injection, XSS, and insecure configurations. The analysis phase involves verifying the findings and determining their potential impact on the application’s security.
Exploitation and post-exploitation
Once vulnerabilities are identified, testers attempt to exploit them to assess the potential damage. This phase helps understand how an attacker could use these vulnerabilities to gain unauthorized access or disrupt services. Post-exploitation involves analyzing the extent of access gained and the possible data compromise, providing insights into the real-world impact of the vulnerabilities.
Reporting and remediation
The final step is documenting the findings in a detailed report. This report includes a description of the vulnerabilities, their severity, and recommendations for remediation. The report helps development and security teams prioritize fixes and implement measures to prevent future occurrences. Effective communication between testers and stakeholders is essential for timely remediation and improving the application’s security system.

Web Application Penetration Testing Process
Don't Be the Next Victim
Secure your most valuable data and assets with Lumiverse Solutions!
Common Challenges and Pitfalls
Lack of skilled resources
A significant challenge in web application penetration testing is the shortage of skilled security professionals. Conducting effective penetration tests requires specialized knowledge and experience. Organizations often struggle to find qualified testers who can thoroughly assess their applications and provide actionable recommendations. Investing in training and partnering with experienced security firms like Lumiverse Solutions can help address this challenge.
False positives and false
False positives and false negatives are common pitfalls in penetration testing. False positives occur when a vulnerability is incorrectly identified, leading to wasted resources on unnecessary remediation efforts. False negatives, on the other hand, occur when actual vulnerabilities are missed, leaving the application exposed to potential attacks. Balancing automated and manual testing helps minimize these issues, ensuring accurate identification of vulnerabilities.
Impact on production systems
Penetration testing can impact production systems, potentially causing downtime or disrupting services. Careful planning and coordination with development and operations teams are essential to minimize this impact. Testing should be conducted during off-peak hours or in a controlled environment to avoid affecting end-users. Communication and contingency planning help manage any potential disruptions and provide a smooth testing process.
Why Choose Professional Security Services
Regular testing schedules
Collaboration between development and security teams
Client Experiences That Shine!
Genuinely robust solutions, effectively detected and neutralized potential threats, providing a sense of confidence in the ever-evolving landscape of cybersecurity. The responsive customer support and commitment to staying ahead of emerging risks make them a reliable choice for businesses seeking top-notch protection.