Securing the Cloud: A Strategic Assessment for Robust Defense
A cloud security assessment services is a comprehensive evaluation aimed at identifying vulnerabilities, risks, and compliance gaps within cloud-based systems. This process involves analyzing risk factors, scanning for security weaknesses, ensuring adherence to regulatory standards, reviewing configurations, and performing penetration tests.
Overview of Cloud Security Assessment Process Services
Network Penetration Testing, also known as pen testing or ethical hacking, is a visionary security measure where simulated cyberattacks are conducted to identify and handle vulnerabilities in a network.
This process helps organizations find weaknesses in their network security and provides actionable insights to strengthen defenses. Using penetration testing services, businesses can actively address security gaps before hackers manipulate them.

Importance of Assessing Cloud Infrastructure and Configurations
Assessing cloud infrastructure and configurations is important for ensuring the security and integrity of data stored and processed in the cloud. This process helps identify misconfigurations, unauthorized access points, and other vulnerabilities that cyber attackers could manipulate. Regular cloud security testing and analysis enables organizations to mitigate risks, comply with regulatory requirements, and maintain customer trust by protecting sensitive information.
Key Objectives and Benefits of Cloud Security Assessment Services
The primary objectives of a Cloud Security Assessment are to identify security gaps, evaluate the effectiveness of existing controls, and provide a roadmap for improvement.
Cloud security assessment benefits by providing improved data protection, compliance with industry standards, and reduced risk of data breaches. Organizations can secure a strong security position and protect assets and reputation by adopting cloud security assessment services.
Overview of Prevalent Cloud Security Threats
Cloud environments are exposed to a range of security threats, including data breaches, misconfigurations, insider threats, and account hijacking. These threats can compromise sensitive data and disrupt business operations. A detailed cloud security evaluation helps organizations understand and address these risks, ensuring the protection of their cloud assets.
Examples:
Data breaches can occur due to vulnerabilities in cloud infrastructure, leading to unauthorized access to sensitive information. Misconfigurations, such as improper access controls or unsecured APIs, can expose data to cyber threats.
Insider threats involving employees or contractors with malicious intent hold powerful risks. Identifying and mitigating these vulnerabilities through cloud security testing is important for maintaining a secure cloud environment.
Real-World Consequences of Inadequate Cloud Security Measures
Inadequate cloud security measures can result in extreme consequences, including financial losses, legal penalties, and reputational damage. Data breaches can lead to loss of customer trust and hefty fines for non-compliance with regulations.
Misconfigurations and insider threats can disrupt business operations and expose critical data to cybercriminals. A comprehensive cloud security assessment helps prevent such incidents by identifying and addressing security weaknesses.
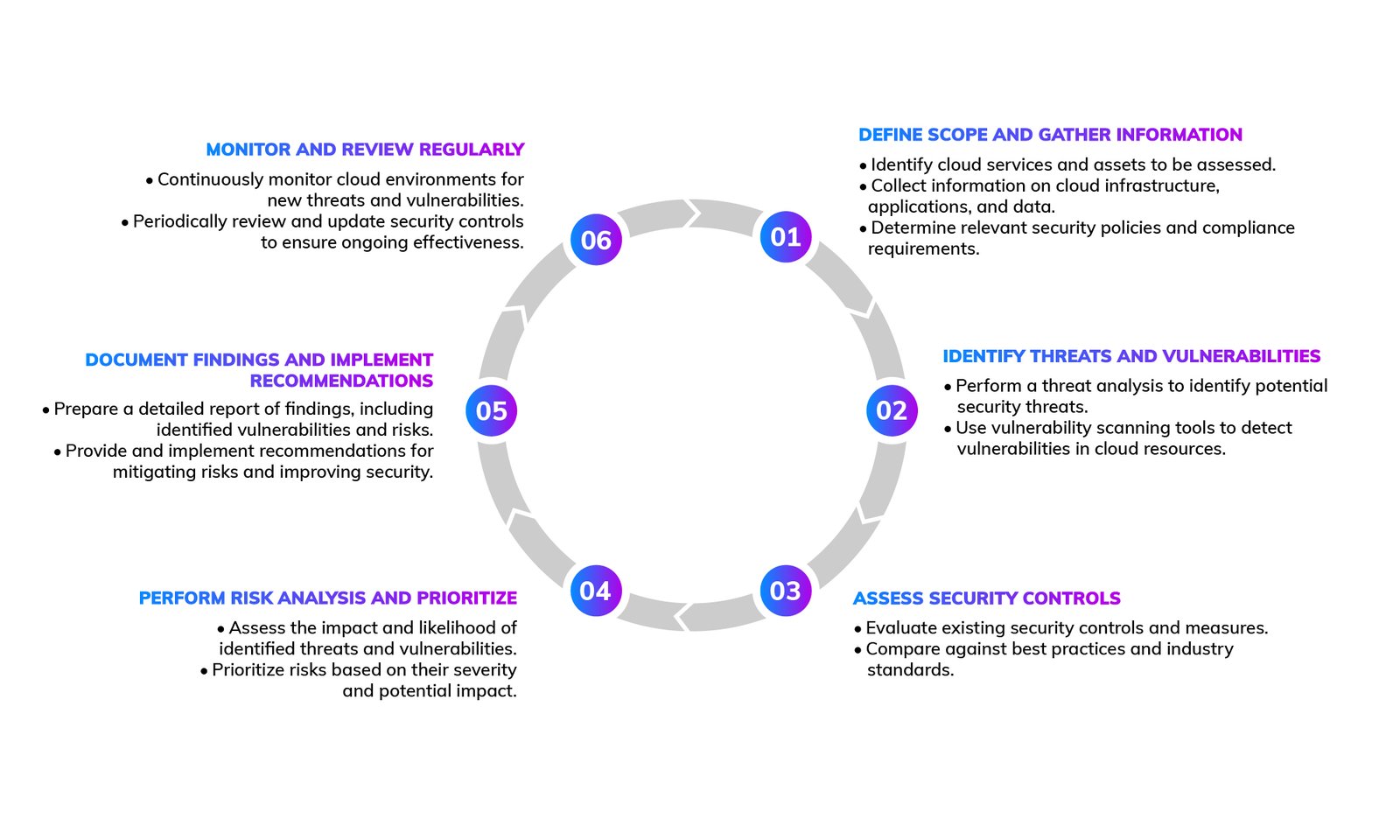
Process of Cloud Security Assessment Services
Don't Be the Next Victim
Secure your most valuable data and assets with Lumiverse Solutions!
Leveraging Best Practices for Cloud Security
Implementing Robust Access Controls
Implementing strong access controls and identity management is essential for securing cloud environments. This involves implementing multi-factor authentication, role-based access controls, and regular review of access permissions.

Encrypting Data in Transit and at Rest
Encrypting data in transit and at rest is a fundamental best practice for cloud security. Data encryption assures that even if data is intercepted or accessed by unauthorized users, it remains unreadable without the decryption key. Executing strong encryption protocols for both data in transit and at rest helps protect sensitive information.
Regularly Auditing and Monitoring Cloud Environments
Regular auditing and monitoring of cloud environments is required to maintain security. Continuous monitoring helps detect suspicious activities, unauthorized access attempts, and potential security incidents in real time. Regular audits ensure compliance with security policies and identify areas for improvement.

