Database Security Assessment Services – Lumiverse Solutions
Ensure the protection of your critical data and applications with Lumiverse Solutions’ Database Security Assessment services. As cyber threats evolve, it’s crucial to implement proactive measures to protect your cloud and on-premise databases from vulnerabilities, breaches, and unauthorized access. Our expert team identifies vulnerabilities, assesses risks, and provides actionable insights to safeguard your organization’s sensitive data.
Overview of database security assessment Services
Database security assessment Services involves assessing the security of your database systems to identify and mitigate vulnerabilities. This process ensures that sensitive data stored in databases is protected from unauthorized access, breaches, and other security threats. It includes analyzing database configurations, user permissions, and data encryption practices.
A Database Security Assessment Services is a critical process that evaluates an organization’s database environment to identify and address vulnerabilities, misconfigurations, and risks that could expose sensitive data to unauthorized access or breaches. This assessment examines key aspects such as access control, user privileges, database configurations, and vulnerability management to ensure that all security controls align with best practices. It also includes the assessment of encryption protocols, logging mechanisms, and backup procedures, verifying that data is encrypted both at rest and in transit and that logging captures any suspicious activity for prompt response.

Why Choose Lumiverse Solutions for Your Database Security Assessment?
Proven Expertise in Database Security
Our team of certified cybersecurity professionals brings years of expertise in database security and penetration testing. We have successfully helped numerous businesses in India safeguard their critical data and achieve compliance with global regulations.
Industry-Leading Tools and Techniques
We use advanced security tools such as Nessus, SQLMap, and DBShield to conduct thorough database assessments. These tools provide powerful insights into your database’s security posture, enabling us to identify and mitigate risks efficiently.
Tailored Solutions for Every Business
At Lumiverse Solutions, we understand that every organization is unique. Our database security assessments are tailored to meet the specific needs of your business, ensuring that all potential vulnerabilities are addressed.
Comprehensive Compliance Support
We help businesses comply with industry regulations like GDPR, HIPAA, and PCI DSS, ensuring that your databases are secure and compliant. Our services help protect against regulatory fines, data breaches, and loss of customer trust.
Continuous Monitoring and Remediation
We offer ongoing support and monitoring to ensure your databases remain secure over time. Our continuous monitoring services detect and mitigate potential threats in real-time, ensuring that your data remains safe from evolving cyber threats.
2 Common Database Vulnerabilities
SQL Injection (SQLi)
SQL injection is one of the most common and dangerous vulnerabilities in database security. This vulnerability occurs when an attacker is able to manipulate a database query by injecting malicious SQL code into an application’s input fields. Once the attacker’s code is executed, they can potentially:
Bypass authentication mechanisms, gaining unauthorized access to sensitive data.
Extract, modify, or delete data from the database, leading to data loss or corruption.
Execute administrative operations, such as shutting down the database or altering critical system settings.
SQL injection attacks can be executed through web forms, URL parameters, or cookies, making it a significant threat to web applications and databases connected to the internet. The best defense against SQL injection is to sanitize user input, use prepared statements with parameterized queries, and implement proper access controls.
Misconfigurations
Database misconfigurations are another prevalent vulnerability. These occur when a database is incorrectly configured, leaving it open to exploitation. Common misconfigurations include:
Default settings that leave sensitive data exposed or provide excessive user privileges.
Unencrypted database connections, leaving data vulnerable to interception and compromise during transmission.
Improper access controls or excessive permissions granted to users, enabling unauthorized access or misuse of data.
Misconfigurations are often the result of rushed setups, lack of security awareness, or failure to follow best practices during installation and maintenance. It is essential to regularly review database configurations, disable unnecessary features, and ensure that only authorized users have access to sensitive data.
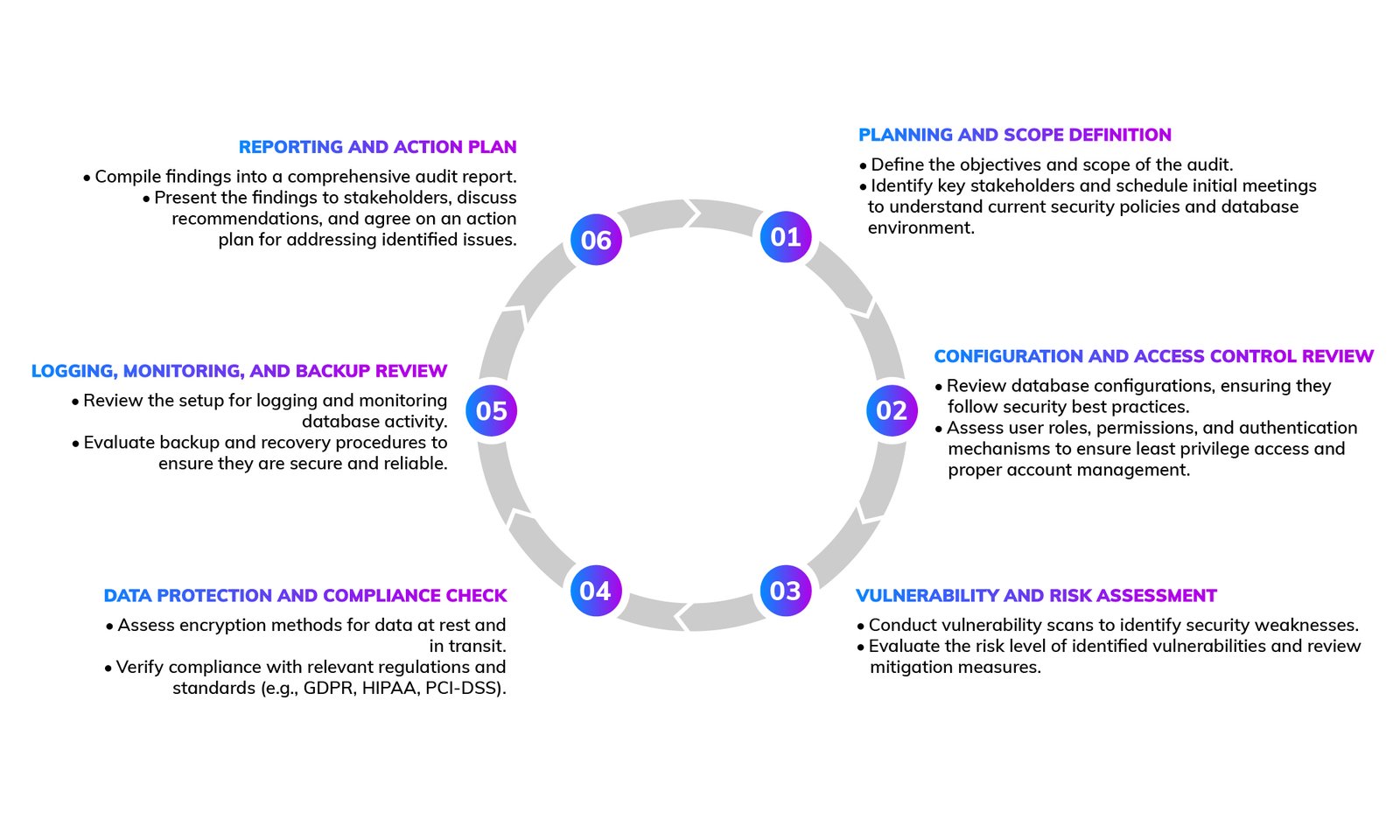
The Database Security Assessment Process
Don't Be the Next Victim
Secure your most valuable data and assets with Lumiverse Solutions!
Tools and Techniques for Database Security
Nessus
Nessus plays a pivotal role in our security assessments by scanning your systems for vulnerabilities and configuration issues that could expose your databases to attack. It is particularly effective in detecting outdated software, missing patches, and weak security settings. Nessus enables us to spot potential risks such as SQL injections and cross-site scripting (XSS) vulnerabilities, providing you with detailed, actionable recommendations to mitigate those risks. It ensures that your database systems are fortified against cyber threats by highlighting security weaknesses before they can be exploited.
SQLMap
To further enhance our testing process, we rely on SQLMap, an essential tool used to detect SQL injection vulnerabilities in your web applications and database systems. SQL injection remains one of the most common and dangerous threats to database security, and SQLMap helps us automate the identification of these weaknesses. By simulating real-world attacks, SQLMap allows us to gauge the impact of a potential attack on your sensitive data, providing us with invaluable insights into possible breaches and vulnerabilities.
DBShield
Another crucial tool in our security assessments is DBShield, a real-time database security tool designed to monitor activity and protect databases from malicious intrusions. With DBShield, we continuously monitor your database systems for anomalies, unauthorized access, and any suspicious activity. This tool acts as an intrusion detection system, capable of blocking potential threats in real-time. It enables us to detect attacks as they unfold, helping us take immediate action to prevent data breaches and ensure the integrity of your database.
Why Choose Professional Security Services
Compliance with industry regulations
Professional penetration testing services ensure that your mobile application complies with industry standards, such as the OWASP Mobile Top 10. Adhering to these standards helps protect user data and reduces the risk of security breaches. Compliance demonstrates your commitment to security and builds user trust.

